Wanna write something very personal and yet there are a kabillion chances of anyone else reading it?
Use this code , and write whatever you want to….but only to the one who knows the way to cypher it , otherwise ……….. never mind , here goes-
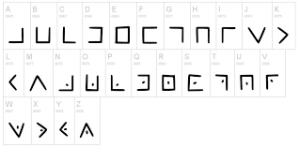
The Pigpen Cipher was used by Freemasons in the 18th Century to keep their records private. The cipher does not substitute one letter for another; rather it substitutes each letter for a symbol. The alphabet is written in the grids shown, and then each letter is enciphered by replacing it with a symbol that corresponds to the portion of the pigpen grid that contains the letter.

Comments
Post a Comment